
VMware Carbon Black Use-Case
- Next-Generation Antivirus
- Enterprise AV Replacement
- Ransomware Protection
- Securing Workloads
- Malware & Non-Malware Protection
- Risk & Compliance
- Threat Hunting
- Incident Response
- Locking Down Critical Systems
- POS, Fixed Function & Industrial Control Systems
- Vulnerability Management
Next-Generation Antivirus
Stops Known and Unknown Attacks
NGAV is designed to replace traditional AV, stopping the full spectrum of modern cyberattacks and providing the detection and response capabilities needed to address every threat. NGAV uses a fundamentally different approach to detect and block malicious activity, taking a complete system-centric view of endpoint security rather than simply focusing on point-in-time malware threats.
How Does Carbon Black Help?
- Stops Known and Unknown Attacks
Innovative streaming prevention technology stops ransomware, malware, and non-malware attacks. - Real-Time Detection
Integrated detection and response alerts you of suspicious activity—which helps you quickly isolate and remediate threats. - Lightweight & Easy
Cloud-delivered agents deploy seamlessly, while a dynamic console shows everything you need to know at a glance.
Back to Top
Enterprise AV Replacement
Assess Your NGAV Readiness
To stop attacks in progress enterprises need to invest in emerging endpoint security platforms like next-generation antivirus (NGAV) that incorporate endpoint detection and response (EDR). However, they must ensure the platform is enterprise-ready, able to withstand the scalability demands and administrative requirements inherent to large organizations.
This whitepaper helps enterprises guide their upcoming discussions about NGAV + EDR solutions. However, they must ensure the platform is enterprise-ready, able to withstand the scalability demands and administrative requirements inherent to large organizations.
Prevent Attacks and Stop Breaches
Due to the increased opportunity for financial gain, cyber criminals invest significant time and resources into creating advanced attacks to target enterprises.
- Blocks custom-built threats targeted at enterprises
- Prevents sophisticated non-malware attacks that bypass traditional AV
- Enables you to future-proof your ransomware defenses
Fastest Investigation & Response
During a response scenario, every minute counts. The longer it takes to address an issue, the more risk your business faces.
- Respond Quickly to reduce exposure to ongoing threats
- Remediate Precisely on any endpoint from a central console
- Reduce Downtime and get users online without calling IT
Easy Operation at Enterprise Scale
Enterprises face a shortage of skilled security professionals, and security teams spend too much time gathering the information they need, limiting the time available to perform true security analysis.
Intelligence and automation in CB Defense optimizes your entire security team
- Hands-free management of devices and policies at enterprise scale
- Automation of complex remediation tasks for speed and reliability
- Integration with existing security stack to share data wherever it’s needed
Back to Top
Ransomware Protection
CB Defense Earns Perfect Score on Comprehensive Ransomware Test
CB Defense participated in a broad-based test conducted by independent security firm MRG Effitas against a comprehensive set of fresh and prevalent commodity, master-boot infector, file-less and other types of samples from 42 crypto-ransomware families collected in the wild. CB Defense stopped every sample. Read the report for complete methodology and
detailed results.
Ransomware Roundup
Today's ransomware is innovating at a rapid pace. Going beyond simple file encryption, ransomware increasingly leverages unknown variants and file-less techniques. Learn more about these new techniques and how Carbon Black stops them.
How Does Carbon Black Help?
- Streaming Ransomware Prevention
Advanced prevention stops current and future ransomware variants by monitoring streams of events related to a ransomware outbreak. - Protects Against New & Emerging Threats
Lures all types of ransomware into a trap, even unknown and file-less varieties, to spot it and stop it before it attacks critical files and shares. - Powerful Application Control
Application control is the most effective way to prevent all forms of ransomware from running on servers and critical systems.
Ransomware Epidemic: Stop Bad Rabbit In Its Tracks
Ransomware isn’t new. In fact, it’s 30-years-old. What IS new is ransomware’s sudden rise as a favored attack by cyber criminals. Like WannaCry and NotPetya before it, Bad Rabbit is yet another example of an aggressive sample of ransomware that has made a huge impact on the security world in a short time.
Be prepared for the next ransomware outbreak
The recent Petya/NotPetya and WannaCry outbreaks have made one thing perfectly clear: ransomware can bring an organization to its knees. Innovation across all aspects of ransomware have allowed these attacks to infect hundreds of thousands of machines in a matter of hours.
Back to Top
Securing Workloads
Traditional Security is Failing to Protect the Datacenter
As applications have become more distributed and more dynamic, they have become more difficult to secure. Traditional security is failing to protect virtualized infrastructure for several reasons:
- Traditional defenses can’t keep up
...especially with non-malware attacks becoming more common and severe, including increasing lateral movement into the data center and hijacking of known-good applications. Traditional data center security controls aligned to infrastructure lack an understanding of data center applications, and are not realistically capable of monitoring east-west flows to prevent lateral attacks. - Security and IT teams lack visibility and a common source of truth,
...as they don’t have shared visibility into their environment, or context for applications including dependencies, how they communicate, or the blast radius of something goes wrong. This lack of situational awareness for data center applications and associated east-west flows creates holes that lead to longer time to discovery, longer time to respond, and longer time to remediation. - There are too many security tools,
...each with its own backend console, policies, configurations, alets, and costs. This creates an overly complex environment that is challenging to maintain and integrate, severely impacting performance and uptime. Security and IT teams have siloed information and disparate tools, causing problems with security implementation, response times, and even compliance.
Securing The VirtualData Center
The data center contains the most sensitive data an organization has, but traditional security solutions do not provide the protection that sensitive data requires. Creating additional challenges, SecOps and Infrastructure teams struggle to find the balance between security and performance. Organizations need a solution that protects applications and the sensitive data they store, while being optimized for the dynamic nature of the virtualized data center.
What You Should Know about Securing Your Virtualized Infrastructure
Applications in the software-defined data center are becoming more distributed and dynamic than ever. VMware and Carbon Black's combined solution pioneers a new approach to endpoint security for your virtualized environment where traditional AV has generally failed to keep pace.
- Application-centric security management makes it easier to secure critical business data and establish baseline intended state behavior
- Reduce business impact by providing IT and Security teams with shared visibility into the application context and criticality of individual VMs
- Leverage the hypervisor to secure data center applications and remediate threats with precision to maintain business continuity
- Protect against lateral movement and datacenter-focused attacks by taking a layered security approach, increasing visibility at all levels, and implementing endpoint protection that actively disrupts attacker behavior
- Significantly strengthen your security posture by supporting alignment between IT and Security teams through shared visibility into the environment
How Carbon Black Helps
Carbon Black offers a purpose-built security solution for protecting applications deployed in the virtualized data center. Jointly architected with VMware, the solution seamlessly integrates with VMware AppDefense and provides:
- Streaming prevention that can stop malware and non-malware attacks
- Live Response that allows administrators to secure remote shell into any protected server to perform full investigations and remediations in minutes
- Complete visibility into blocked and detected attacks to show what happened, where it came from, and which machines were affected
- Complete detection and response capabilities in a single agent and console
- A lightweight agent that does not impact end user performance
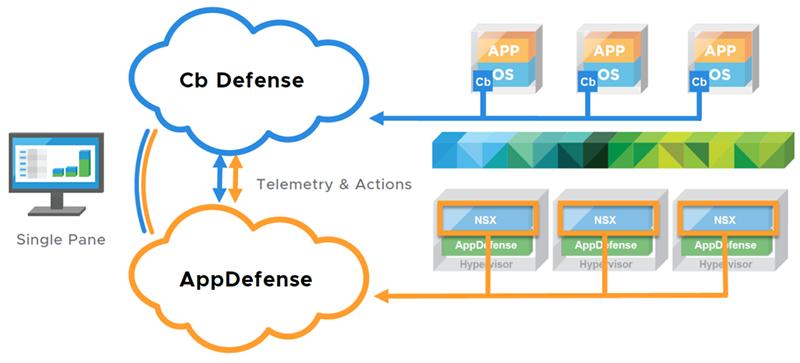
All these services are delivered through the CB Predictive Security Cloud — the endpoint protection platform that consolidates
security in the cloud using a single console and lightweight agent that has little impact on end users.
Back to Top
Malware & Non-Malware Protection
Stop Non-Malware Attacks
Stopping a non-malware attack requires a different approach than traditional methods that stop malicious files at a single point in time. Since non-malware attacks leverage a series of known, allowed applications and processes, the entire event sequence must be analyzed to uncover the threat.
How Does Carbon Black Help?
- Stops Advanced Attacks
Innovative streaming prevention technology stops ransomware, malware, and non-malware attacks. - Clear Threat Visibility
Powerful attack visualizations display the entire kill chain, so you can quickly understand the root cause and remediate. - Lightweight & Easy
Cloud-delivered agents deploys seamlessly, and a dynamic console shows everything you need to know at a glance.
Back to Top
Risk & Compliance
New regulations have forced organizations around the globe to rethink data privacy and protection.
To meet the new standards, visibility into all endpoint activity is essential to get critical information that will reduce risk, lower liability, and prove security control assurance across the cybersecurity kill chain.
How Does Carbon Black Help?
- Accelerate Time to Successful Audit
Reduce liability at all levels with IT audit and risk controls that give you the intelligence needed to accelerate gap analyses by nearly eliminating the pre-compliance data gathering process - Prove Security Control Assurance
Ensure a state of continuous compliance by showing that security controls are working effectively and in place following ANY change in your environment with file integrity monitoring and control - Communicate Risk to Executives
Take a positive and prioritized approach to reducing your organization’s attack surface and addressing regulatory gaps with actionable business intelligence needed for board-level security investment decisions
CB Cloud Audit and Remediation
Back to Top
Threat Hunting
Attackers are Getting Smarter
In today’s world, it’s no longer a matter of if you’ll face a cyberattack, but when. To prevent this, threat hunting has emerged as an essential process for organizations to preempt destructive attacks.
The people defending your organization are your best chance at staying a step ahead of your adversaries. While it may seem aggressive to work on the “assumption of breach,” the reality is that attackers may be inside a network for days, weeks and even months on end, preparing and executing attacks, without any automated defense detecting their presence. Threat hunting stops these attacks by seeking out covert indicators of compromise (IOCs) so attacks can be mitigated before the adversary can achieve their objectives.
Join a Live Demo of CB ThreatHunter on the VMware Carbon Black Cloud™
Join us the third Wednesday of each month at 1:00 PM EST (10:00AM PST) for our 45-minute PSC live demo to learn how to:
- Stop the headline breach and detect advanced attacks faster
- Proactively explore your environment for abnormal activity
- Leverage cloud-native threat intelligence and custom watchlists to automate repetitive hunts
Threat Hunting Basics
SOC and IR teams need a way to dive deeper into the data to make their own judgments.
Threat hunting reduces the cost of a breach. In the event that you do need to respond to an incident, the fact that you’ve been threat hunting — and have already collected and centralized all the endpoint data in your environment — will significantly reduce the time and money you spend responding and remediating. The average total cost of a breach is $3.86 million, and breaches that take over 30 days to contain can cost companies an extra $1 million.
Threat hunting allows you to find gaps and fine tune your environment. 91% of organizations reported improvements in speed and accuracy of response as a direct result of their threat hunting practices.
Advanced Threat Hunting
Threat Hunting Requires the Right Data
77% of respondents to a recent SANS Survey said that endpoint data was critical for conducting proactive threat hunts. If you are only deploying scan-based technologies on the endpoint, or rely on a tool that filters out information not known to be malicious yet, you are leaving gaps in your data collection coverage, and losing the full context of any attack. When preparing to hunt for threats, ensuring that your endpoint security tools can continuously collect all the critical data necessary to conduct immediate and conclusive threat discovery is indispensable.
Combing through logs and SIEM data for indicators of compromise (IOCs) can be tedious, time consuming and expensive. By proactively capturing and storing all unfiltered endpoint activity, whether known to be bad or not, enterprises can instantly leverage a comprehensive historical record of their environment for effective threat hunting.
How can Carbon Black Help?
Carbon Black offers threat hunting capabilities through the VMware Carbon Black Cloud, the endpoint protection platform that consolidates security in the cloud using a single nd lightweight agent that has little impact end users. The PSC delivers scaleable hunting; this sophisticated detection combines custom and cloud-native threat intel, automated watchlists, and integrations with the rest of your security stack to efficiently scale your hunt across the enterprise
- Proactively explore your environment for abnormal activity
- Leverage cloud-native threat intelligence and custom watchlists to automate repetitive hunts
- Use the platform’s open APIs and out-of-the-box integrations to correlate data across your security stack
Threat Hunting Tools
Whether you are investigating past activities or searching in real time, Carbon Black provides the tools you need to hunt threats across your enterprise.
CB Cloud Audit and Remediation
Back to Top
Incident Response
Increase Visibility to Respond Faster
Incident response is about getting answers quickly. To start, you need the details of all endpoint activity available to you at all times. This allows your responders to visualize the attack, see it evolve, and determine the root cause of an infiltration and its intended targets. With complete visibility, you'll be able to quickly find conclusive answers to the questions you're asking.
How Does Carbon Black Help?
- Cuts Investigation Time
Continuously record endpoint activities and store centrally for rapid access. "Roll back the tape" at any time, often shortening investigation time from days to minutes. - Reduces Overhead
Live Response allows you to remotely investigate and remediate any endpoint, drastically reducing IT overhead and the need for reimaging. - Unparalleled Threat Visibility
Detailed process trees reveal the root cause of every attack, so you can quickly close security gaps and stop future attacks.
CB Cloud Audit and Remediation
Back to Top
Locking Down Critical Systems
They Are 'Critical' for a Reason
Critical systems are increasingly targeted because they contain the most valuable information. These systems cannot afford a moment of unscheduled downtime or performance degradation as they are the lifeblood of the organization. Companies whose systems hold highly sensitive data must utilize a solution that can guarantee their data won’t be breached or stolen.
Reducing Risk
There are compensating controls that businesses can implement to help reduce the risk to their critical servers. Some of the key methods are virtualization, and application control/whitelisting.
Virtualization
Hosting assets within a virtualized environment can provide a number of security benefits; increased control over critical assets, ease of re-imaging in the event of a compromise, and the ability to limit critical server exposure to an environment. If an asset becomes a target, it can be quickly isolated and re-initialized. but for critical servers running applications that require round-the-clock access, virtualization represents a possibility of increased administration and resources. It can also lead to failed compliance policies by virtue that in-scope data must be controlled or cannot run within a virtual environment.
Application Control and Whitelisting
Application whitelisting is a security model focused on allowing known “good” applications to run rather than blocking known “bad.” By only allowing trusted software to run, application whitelisting will stop exploits and reduce the administration associated with system and application patching and updates. In “default-deny” mode, application whitelisting is a highly effective compensating control to meet regulatory compliance standards and harden out-of-date systems.
How Does Carbon Black Help?
CB Protection was the only solution to stop 100% of attacks in NSS Labs 2017 Advanced Endpoint Protection (AEP) test.
- Lock Down
Systems Stop malware, ransomware, and zero-day attacks - Block Unauthorized Change
Built-in file-integrity monitoring, device control, and memory protection - Harden Critical Systems
Support for embedded, virtual, and physical OSes
Back to Top
POS, Fixed Function & Industrial Control Systems
Block Attacks Against Industrial Systems
Protecting hardened and fixed-function devices like point-of-sale (POS) and industrial control systems is challenging; they use a wide variety of specialized operating systems and support specific, nonstandard applications and protocols. These devices require flexible policies, effective enforcement, and lightweight agents to stay protected without compromising usability or uptime.
How Does Carbon Black Help?
- Powerful Application Control
Application control flips the traditional paradigm on its head—it blocks everything that isn't specifically pre-approved by both your IT- and cloud-driven policies. - Low-Touch Whitelisting
Stop next-generation attacks and prevent unwanted change on your critical systems. - Protect Industrial Control Systems
Real-time visibility and customizable signature-less protection helps you defend industrial control systems against persistent threats.
Back to Top
Vulnerability Management
Reduce the Attack Surface
Reduce the attack surface and simplify operations with prioritized vulnerability reporting and continuous visibility across your environment.
How Does Carbon Black Help?
- Offload Computation to the Cloud
Real-time vulnerability assessment reduces the need for resource-heavy scans, with no additional data collection and analysis is performed on your devices. - Leverage Context
Leverage existing capabilities of Carbon Black’s sensor across your environment to gather asset context with Audit and Remediation and correlate attacks to vulnerabilities via EDR alerts. - Reduce Overhead
Deliver functionality natively with the built-in Carbon Black sensor. No additional agents to deploy, manage, and maintain.
